top of page



What is a Ransomware and How to protect from it
Keeping your computer safe from malware on the internet has become problematic in recent years, and one of the most egregious types of...
douiriothmane
Aug 5, 2023


SASE Component Fundamentals
If you work in networking and security, you will likely encounter SASE. We pronounce it “sassy,” and it stands for Secure Access Service...
douiriothmane
Jul 28, 2023


How To Fully Benefit From a NGFW (Next-Generation Firewall)
As all cybersecurity professionals know, cybercriminals are becoming increasingly sophisticated and skilled at breaching networks and...
douiriothmane
May 4, 2023


What is VxLAN and when you might need it?
If you have been exposed to networking terminologies before, you probably heard of LAN and VLAN terms and what they mean. How about...
douiriothmane
Apr 25, 2023


8 Things to Consider before migrating to Wi-Fi 6
Wi-Fi is a huge part of our lives. We all use it in our homes and offices, and it is essential for our smart devices like mobile phones...
douiriothmane
Mar 29, 2023


Benefits of SD-WAN
SD-WAN has gained a large popularity and adoption in the last decade. While it is not a replacement for traditional WAN circuits, ....
douiriothmane
Jan 7, 2023

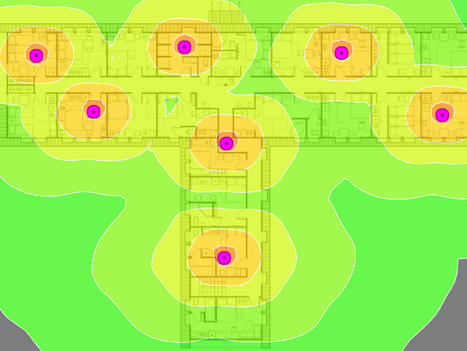
Difference between a predictive and a validation survey in Wi-Fi
Wi-Fi is a networking technology that uses radio waves to allow high-speed data transfer over short distances. It is usually the first...
douiriothmane
Jan 4, 2023


What is Zero Trust Network Access (ZTNA)?
What is ZTNA? Zero Trust Network Access (ZTNA) is an approach to network security. It is based on verifying the trustworthiness of...
douiriothmane
Jan 2, 2023


How Partnering With a (IT) Managed Service Provider Can Help You in Running Your Business
In today’s highly competitive business environment, Information Technology (IT) has gone beyond mere working tools; it is now a critical...
douiriothmane
Dec 30, 2022
bottom of page